![[Digital logo]](../../IMAGES/DIGITAL-LOGO.GIF)
![[HR]](../../IMAGES/REDBAR.GIF)
![[Digital logo]](../../IMAGES/DIGITAL-LOGO.GIF)
![[HR]](../../IMAGES/REDBAR.GIF)
An OpenVMS system can support both TCP/IP and OSI capabilities on the
same system. OSI protocols are incorporated in Digital's DECnet
software (DECnet-Plus for OpenVMS), which can run concurrently with
TCP/IP networking products on the same OpenVMS system.
2.1.2 Comparing the OSI Model with the TCP/IP Model
In comparing the TCP/IP model with the OSI model, TCP/IP can be viewed as supplying the functions of layers 3 and 4 of the OSI model. TCP/IP provides a number of protocols for the internet layer (corresponding to layer 3, the network layer, of the OSI model) and the transport layer (corresponding to layer 4, the transport layer, of the OSI model).
As shown in Figure 2-1, however, the TCP/IP model does not follow the OSI model exactly for all layers. For the upper-level layers, TCP/IP applications provide the services of the presentation and session layers of the OSI model. In addition, TCP/IP does not provide specific protocols for the bottom two layers that correspond to the physical layer and the data link layer of the OSI model. Instead, TCP/IP interfaces with whatever protocols are available for the physical network and the network interface.
Implementation of the OSI model places emphasis on providing a reliable data transfer service, while the TCP/IP model treats reliability as an end-to-end problem. Each layer of the OSI model detects and handles errors; all data transmitted includes checksums. The transport layer of the OSI model checks source-to-destination reliability.
In the TCP/IP model, reliability control is concentrated at the transport layer. The transport layer handles all error detection and recovery. Individual hosts or links can lose data without making any attempt at recovery. Corrupted datagrams can be discarded at internal gateways, and datagrams can be rerouted or dropped if network line problems occur. The TCP/IP transport layer uses checksums, acknowledgments, and timeouts to control transmissions and provides end-to-end verification.
Another contrast between the OSI model and the TCP/IP model is the role of the host system. Hosts on OSI implementations do not handle network operations, but TCP/IP hosts participate in most network protocols. TCP/IP hosts carry out such functions as end-to-end verification, routing, and network control. The TCP/IP internet can be viewed as a data stream delivery system involving intelligent hosts.
The following sections describe TCP/IP networking design, including the
functions of the different layers and protocols.
2.2 TCP/IP Design
Table 2-1 lists the layers into which the TCP/IP model organizes TCP/IP software functions. Figure 2-2 shows the TCP/IP layers and the protocols supported at each layer. Data can pass successively through the layers of the TCP/IP software, and each layer adds information to the message being transmitted to the remote host. If intervening hosts are required to route the data through the network to the other host, only the lower layers (the physical network, the network interface, and possibly the internet layer) are involved.
| TCP/IP Layer | Function |
|---|---|
| Application layer | A user invokes an application program that accesses a service available across a TCP/IP internet. The application passes data to and receives data from the transport layer. Protocols available at the application layer are described in Section 2.3. |
| Transport layer | This layer provides services that permit an application program on one host to communicate with an application program on a remote host. The transport layer divides the stream of data into packets, adds a destination address, and passes the packets to the next layer. The transport uses two protocols, TCP and UDP, described in Section 2.4. |
| Internet layer | This layer ensures that data is routed to the correct destination. The internet layer encapsulates the packet received from the transport layer into a datagram, adds a header, and determines the routing requirement. For incoming datagrams, it determines which transport protocol should handle the packet. The internet layer uses the Internet Protocol (IP), as described in Section 2.5. |
| Network interface layer | This layer controls access to network transmission mechanisms. The network interface is responsible for accepting IP datagrams and transmitting them over a specific network. The interface can be a device driver (connected to a LAN) or a subsystem with its own data link protocol. |
| Physical network | The hardware connection provides the physical interconnection between the host and the network. |
Figure 2-2 TCP/IP Layers and Protocols
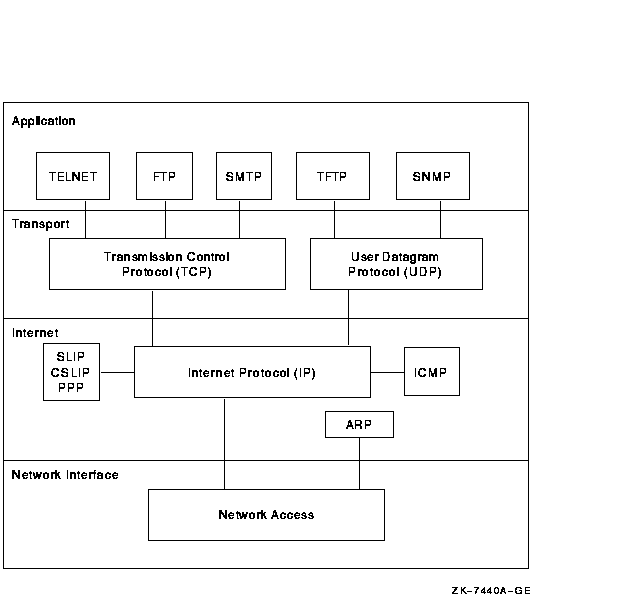
The application layer includes all processes and services that use the transport layer to deliver data. The most widely-known applications protocols are:
Application programs send messages (streams of data) to the transport layer protocols UDP and TCP. An application is designed to choose either UDP or TCP based on the services it needs. An application chooses:
When an application sends a message to the transport layer, UDP and TCP break the information into packets, add a packet header (which includes a destination address), and send the information to the network layer for further processing. Other protocols and applications use UDP to make datagram connections and TCP to make stream connections. The socket interface implements these protocols.
UDP and TCP use IP, the underlying protocol, to transport datagrams.
Both allow programs to send messages to and receive messages from
applications on other hosts, and both use protocol
ports (abstract destination points) on the host to identify
the specific destination of the message. These protocol ports receive
and hold messages in queues until applications can retreive them.
2.4.1 Transmission Control Protocol
TCP provides reliable stream delivery of data between Internet hosts. Unlike UDP, TCP ensures that data is not damaged, lost, duplicated, or delivered out of order to a receiving process. Because of this transport reliability, application programmers are not required to build communications safeguards into their software.
TCP supplies the following services in carrying out end-to-end verification between the source and destination for detection and recovery of lost datagrams:
Before the transmission of data, TCP establishes a connection between the two transport layers through the exchange of messages. Because multiple application programs can run on a single host, TCP uses protocol port numbers to distinguish among the multiple destinations within a given host computer. A specific port on a host can be addressed by a client to request a specific service. To identify a connection, TCP specifies a pair of end points, defining each end point as consisting of a host IP address and a TCP port on that host.
The following application protocols use TCP:
TELNET and FTP applications are described in Chapter 3.
2.4.2 User Datagram Protocol
UDP is an alternative transport mechanism that relies on the underlying IP to send its datagrams and provides the same connectionless message delivery as IP. UDP does not guarantee that the data will be delivered. Applications that use UDP must have built-in safeguards to discover that a datagram was delivered out of sequence or not delivered. UDP allows the sender to specify source and destination port numbers for the message and also calculates a checksum of both the data and the header. These two features allow the sending and receiving applications to ensure the correct delivery of a message.
UDP permits an application to send a message to a destination application on another network without requiring that the destination application be active when the message is sent. UDP sends datagrams, but does not guarantee delivery or protection against duplicate datagrams. The message delivery is connectionless: UDP considers the delivery complete once the message is placed on the network.
The following protocols can use UDP:
The Internet network-level protocols (IP, ARP, ICMP) handle machine-to-machine communications. These protocols provide for transmission and reception of transport requests and handle network-level control.
The TCP/IP internet layer moves data from one host to another, even if the hosts are on different networks. The internet layers on cooperating hosts are in communication with each other while they move data across a network. Each intervening host along the logical communications path moves the data closer to the destination host.
The primary protocol used to move data is the Internet Protocol (IP), which provides the following services:
IP provides a connectionless method of delivering data from one host to
another. It does not guarantee delivery and does not provide sequencing
of datagrams (packaged in packets). IP attaches a header to the
datagram that includes the source address and the destination address,
both of which are unique internet addresses. If an intervening router
needs to change the size of a message so a router can handle the
message, IP fragments the message into smaller packets that can be
reassembled at the destination host.
2.5.1 IP Routing
IP routing involves using the destination IP address of a datagram to decide where to send the datagram. IP routing passes to the network interface software the IP address of the next machine to which the datagram should be routed. The datagram is encapsulated, the IP address is mapped to a physical address, and the frame is transmitted to the next host.
If the source and destination hosts are in the same network, the
routing is direct. If the datagram must be sent through a gateway to
another network, the routing is indirect. The host sends an indirectly
routed datagram to the nearest gateway; the datagram is then routed
from gateway to gateway until it can be routed directly across a
network to the destination host.
2.5.2 IP Addressing
Each host in a network has a unique IP address that is used in communicating with the host. Addresses, which are assigned by a central agency, are in 32-bit binary format, usually expressed as 8-bit fields separated by decimal points. Each field can have a value from 0 to 255 (for example, 97.0.5.110). IP addresses are divided into the following classes:
A subnet is a network within a network. Organizations
can use subnet addressing to divide an assigned network. For example,
an organization that uses a Class B network number, might choose to
subnet the network to effectively have more than 250 networks by using
8 bits of subnet. The Class B network number becomes a Class C network
number. Subnets can be used to add hosts without disrupting the rest of
the network, especially if the network contains a number of gateways.
2.5.3 Internet Host Names
Each host computing system in a TCP/IP network or internet is identified by a unique host name as well as a unique IP host address. TCP/IP supplies a mechanism for translating the host name to the host address that is required by the IP protocol.
The domain name system (DNS) is one example of a distributed name/address mechanism used in the global Internet. It provides for a hierarchy of host names and distributes host name and address information throughout the Internet. Another example is the BIND Resolver.
The name space for Internet hosts supports hierarchically arranged host names, called domain names. The domain name uniquely identifies a host computer that is connected to the Internet. The top-level domain name in the hierarchy can represent an organizational domain or a geographical domain. In the United States, examples of typical organizational domain names are com (for commercial organizations) and edu (for educational institutions). Internationally, the geographical domain name is a standard two-letter international country abbreviation (such as au for Australia and fr for France).
The top-level domain name can be divided into subdomain names that further identify the host. The subdomain names are arranged to the left of the top-level domain name and are separated by periods. For example, computer-name.company.com is the format.
The Internet address of a user who is logged in to an Internet host is
in the form userid@domain in which userid is the
user's login name.
2.6 Other Internet Layer Protocols
Protocols that interact with the Internet Protocol provide services
that manage data movement problems. The following sections introduce
these protocols.
2.6.1 Internet Control Message Protocol (ICMP)
The Internet Control Message Protocol (ICMP) is an integral part of IP that provides error-reporting mechanisms used for regulating network performance. ICMP performs the following:
ICMP provides feedback about problems in the communications environment, but does not make IP reliable. That is, ICMP does not guarantee that an IP packet will be delivered.
ICMP messages are sent in varying situations, including the following:
SLIP is a minimal protocol used to send datagrams for transmission across a serial line such as a telephone circuit. (SLIP is not an Internet standard.) SLIP is used only when both hosts know each other's address and only when IP datagrams are being transmitted. When a host makes a connection, the SLIP server behaves like a router for TCP/IP traffic. Once connected, the SLIP host sends all network traffic over the serial interface.
Because network traffic is exchanged over the telephone link,
performance is an issue for applications that handle numerous graphics,
file sharing, or hypermedia. Compressed SLIP (CSLIP) improves SLIP
performance by compressing the TCP/IP headers.
2.6.3 Point-to-Point Protocol (PPP)
PPP was developed as an Internet standard to address the weaknesses of SLIP. Often used for dialup remote LAN access, PPP allows the remote host to connect to the network and use IP network protocols. PPP is defined as a three-layered protocol as follows:
ARP translates Internet addresses into hardware addresses. (ARP does not translate addresses for the Serial Line Interface or PPP because SLIP and PPP have no hardware addresses.) ARP dynamically traces Internet addresses to hardware addresses on local area networks and stores this information in a mapping table.
ARP is not generally available to users or applications. When an application sends an Internet packet to an interface driver, the driver requests the appropriate address mapping. If the mapping is not in the table, an ARP broadcast packet is sent through the requesting interface driver to the hosts on the local area network.
When a host that supports ARP receives an ARP request packet, the host notes the IP and hardware addresses of the requesting system and updates its mapping table, if necessary. If the receiving host's IP address does not match the requested address, the host ignores the request packet. If the IP address does match, the receiving host sends a reply packet to the requesting system. The requesting system stores the new mapping and uses it to transmit future Internet packets.
Unlike most protocols, ARP packets do not have fixed-format headers. Instead, the message is designed to be useful with a variety of network technologies.
This chapter summarizes the characteristics of common TCP/IP applications. Software products supplied by Digital and other vendors implement these applications for OpenVMS systems. (See Appendix A for descriptions of currently available TCP/IP products that run as layered products on OpenVMS systems.)
Users on OpenVMS systems running TCP/IP software can invoke certain TCP/IP applications by specifying related OpenVMS DCL commands (as indicated in Table 3-1). Chapter 5 specifies the DCL command formats.
This chapter also describes software tools for retrieving information
on the Internet.
3.1 Commonly Used TCP/IP Applications
Table 3-1 identifies commonly used network applications that are supported by almost all TCP/IP systems. The standard command, which is a UNIX syntax, is traditionally used with TCP/IP. Because this syntax can vary slightly among vendors, and because the syntax can be unfamiliar to OpenVMS users, an alternative syntax was developed jointly with the TCP/IP vendors for OpenVMS. This OpenVMS syntax is consistent with all TCP/IP vendor products and is a layer on OpenVMS commands. Note that the traditional UNIX style commands can also be used.
| Operation | Standard Name | Standard Command | OpenVMS DCL Command |
|---|---|---|---|
| Remote terminal service | RFC 854 and others,¹ Telnet | telnet | SET HOST/TELNET |
| RFC 1282, BSD Rlogin | rlogin | SET HOST/RLOGIN | |
| Remote file access | RFC 959, File Transfer Protocol (FTP) |
ftp>get
ftp>put |
COPY/FTP |
| BSD RCP² | rcp | COPY/RCP | |
| Remote directory listings | RFC 959, File Transfer Protocol (FTP) | ftp>ls | DIR/FTP |
| Point-to-point connections | RFC 1661³ and others, Point-to-Point Protocol (PPP) | pppd | PPPD |
TCP/IP applications follow a client/server model. The client is a program on a host that uses the services of a server located on either the same host or on a different host than the client. Among the most frequently encountered client/server user applications for TCP/IP are TELNET and FTP.
3.2 Remote Terminal Service
Virtual terminal protocol applications provide the TCP/IP application
layer utilities and services that enable each user to log in to a
remote host, using the local terminal as though it were a terminal on
the remote host.
TCP/IP supports two virtual terminal protocols:
Both the TELNET service and RLOGIN utility perform remote login
operations, but in different ways.
3.2.1 Connecting to a Remote Server Using the TELNET Service
TELNET, running on a local computer, enables the user to connect to a specified host through a network that supports TCP/IP connections. TELNET can connect a computer to a remote computer host located anywhere in the world.
The TELNET service supports the telnet command, which allows a user on a client system to connect with a server on a remote system. The default server is the TELNET server that provides an interactive terminal session to execute commands at the remote host. The telnet command uses TCP as the transport protocol to guarantee accurate data delivery.
If the user connects to a TELNET server, a login session begins on the remote system. Once the connection is made, TELNET allows interaction between the user and the remote host. The user's keystrokes pass to the host and the remote computer displays pass to the local terminal. The local keyboard and screen seem to be connected to the remote computer.
In most cases, the user needs an account and password on the remote host in order to use TELNET for logging in to the remote system. Some software products that implement the telnet command also use Kerberos authentication to validate the user's identity (see Section 5.1.1) before granting access to the remote system. Many computers on the Internet provide some type of public TELNET access, permitting users to log in to a special guest account.
The telnet command models the local terminal and the remote terminal into network virtual terminals (simplified ASCII devices with keyboards and printers). Services required by either end of the connection are negotiated between the client and server.
TELNET also permits the local user to connect to an IBM mainframe host over a TCP/IP connection. A special TELNET client supports 3270 mode, which provides for IBM 3270 terminal emulation. When the TN3270 mode is active, the local keyboard emulates the keyboard normally used on an IBM 3270 class terminal. The remote IBM mainframe host must support the 3270 TELNET server.
In addition to the standard telnet command, OpenVMS
users on systems running TCP/IP software can use the alternative
OpenVMS style commands to make TELNET connections. For example, the DCL
command SET HOST/TELNET invokes the TELNET client program (see
Section 5.1.4). The DCL command SET HOST/TN3270 invokes the TN3270
terminal emulator client program (see Section 5.1.5).
3.2.2 Logging In to a Remote Host Using the RLOGIN Utility
The RLOGIN utility permits the user on a local host to run commands interactively on a remote host. The RLOGIN client program on the local host is connected to a remote RLOGIN server through a TCP/IP connection.
A user at a local host invokes the rlogin command. This command logs the user in to a remote host and starts an interactive terminal session. After the session starts, all commands the user enters at the local host are executed by the remote host, while the local host displays all of the output. The login session at the remote host can also be started with the name of a different user. If necessary, an 8-bit path can be established between the local and remote hosts.
The RLOGIN utility allows different hosts to share resources. When a host receives a request for connection, the RLOGIN server validates the source port number and the client user name. If the user validation fails, the RLOGIN server prompts for the user's password and checks the password file on the remote host. Some application products that implement the rlogin command use Kerberos authentication to validate the user's identity (see Section 5.1.1). The Kerberos authentication standard is RFC 1411.
![[HR]](../../IMAGES/REDBAR.GIF)
6436P001.HTM OSSG Documentation 26-NOV-1996 11:22:24.32
Copyright © Digital Equipment Corporation 1996. All Rights Reserved.