![[Digital logo]](../../IMAGES/DIGITAL-LOGO.GIF)
![[HR]](../../IMAGES/REDBAR.GIF)
![[Digital logo]](../../IMAGES/DIGITAL-LOGO.GIF)
![[HR]](../../IMAGES/REDBAR.GIF)
In order to modify a security profile, you need control access to the object. An ACL grants control access explicitly whereas a protection code grants it implicitly to anyone belonging to the owner or system categories. If an object profile is modified while the object is being accessed, the existing access is unaffected.
The following table identifies object classes and the access types they support.
| Object Class | Access Types | |
|---|---|---|
| CAPABILITY (VAX only) | Use, Control | |
| COMMON_EVENT_FLAG_CLUSTER | Associate, Delete, Control | |
| DEVICE | Read, Write, Physical, Logical, Control | |
| FILE (including directory file) | Read, Write, Execute, Delete, Control | |
| GROUP_GLOBAL_SECTION | Read, Write, Execute, Control | |
| LOGICAL_NAME_TABLE | Read, Write, Create, Delete, Control | |
| QUEUE | Read, Submit, Manage, Delete, Control | |
| RESOURCE_DOMAIN | Read, Write, Lock, Control | |
| SECURITY_CLASS | Read, Write, Control, Logical I/O, Physical I/O | |
| SYSTEM_GLOBAL_SECTION | Read, Write, Execute, Control | |
| VOLUME | Read, Write, Create, Delete, Control |
The OpenVMS Guide to System Security provides a full explanation of protected objects and how to modify them.
Table DCLII-22 shows the qualifier categories for the SET SECURITY command. The explanations for the qualifiers following Table DCLII-22 occur in alphabetical order.
| General Qualifiers |
ACL-Modifying Qualifiers | Security Class Qualifier | File-Specific Qualifiers | Transfer Qualifiers |
|---|---|---|---|---|
|
/ACL
/CLASS /LOG /OWNER /PROTECTION |
/AFTER
/DELETE /EDIT /REPLACE |
/PROFILE |
/BACKUP
/BEFORE /BY_OWNER /CONFIRM /CREATED /DEFAULT /EXCLUDE /EXPIRED /MODIFIED /SINCE |
/COPY_ATTRIBUTE
/LIKE |
/ACL[=(ace[,...])]
Identifies one or more access control list entries (ACEs) to add, replace, or delete. Enclose each ACE in parentheses and separate multiple ACEs by commas (,). The most common type of entry, the Identifier ACE, has the format (IDENTIFIER=identifier, ACCESS=access-type(+...)). By default, SET SECURITY adds an ACE to the top of the ACL. This behavior changes when you include one of the positional qualifiers: /AFTER, /DELETE, or /REPLACE. See the discussion of ACL ordering in the OpenVMS Guide to System Security./AFTER=ace
Positions all ACEs specified with the /ACL qualifier after the ACE named with the /AFTER qualifier./BACKUP
Modifies the time value provided with the /BEFORE or the /SINCE qualifier. The /BACKUP qualifier selects files according to the date of their most recent backup (rather than by the creation, expiration, or modification date). By default, SET SECURITY selects files according to their creation date./BEFORE[=time]
Selects only those files dated prior to the specified time. You can specify time as absolute time, as a combination of absolute and delta times, or as one of the following keywords: BOOT, LOGIN, TODAY (default), TOMORROW, or YESTERDAY. Specify the /CREATED or the /MODIFIED qualifier to indicate the time attribute to be used as the basis for selection. The /CREATED qualifier is the default.For complete information on specifying time values, see the OpenVMS User's Manual or the topic SPECIFY Date_Time in online help.
/BY_OWNER[=uic]
Selects files whose owner's UIC matches the UIC specified. The default UIC is that of the current process./CLASS=class-name
Specifies the class of the object whose profile is to be modified. By default, the command assumes the object class is FILE./CONFIRM
Controls whether SET SECURITY prompts for verification before performing the operation. Valid responses are YES, NO, TRUE, and FALSE. Answers are not case sensitive and can be abbreviated to one letter. To stop processing the command at any point, type QUIT or press Ctrl/Z. To cancel the verification procedure but to proceed with the command, type ALL./COPY_ATTRIBUTE=(keyword[,...])
Specifies a subset of security elements to transfer from a source object to a target object. Valid keywords include the following:
Keyword Description ALL (default) Copy all security elements ACL Copy the access control list OWNER Copy the owner PROTECTION Copy the protection code Use the /COPY_ATTRIBUTE qualifier with the /LIKE qualifier. For example, you can create an ACL for an object and then copy its ACL to new objects.
/CREATED
Modifies the time value specified with the /BEFORE or the /SINCE qualifier. The /CREATED qualifier selects files according to the date they were created (rather than by the backup, expiration, or modification date). By default, SET SECURITY selects files according to their creation date./DELETE[=ALL]
Deletes ACEs according to the following rules:
- The expression /ACL=aces/DELETE deletes the named ACEs.
- The expression /ACL/DELETE deletes all unprotected ACEs.
- The expression /ACL/DELETE=ALL deletes all ACEs including protected ACEs.
- The expression /ACL=aces/DELETE=ALL deletes the existing ACL (if any) and create a new ACL with the ACEs specifies on the /ACL qualifier.
/DEFAULT
Regenerates the security profile of a file. The default qualifier changes the protection code, the ACL, and the owner elements of a file to what it would be if the file had just been created. The profile is recreated according to the following rules:
- The protection code is propagated from the default protection ACE on the directory (if one exists), or else it is propagated from the process default.
- The ACL is propagated from the parent directory for those ACEs that have the default option.
- The owner is set to the owner of the parent directory.
With subdirectory files, SET SECURITY assigns the owner, protection, and ACL elements of the parent directory.
SET SECURITY does not copy any ACE on the source object if the ACE holds the nopropagate attribute nor does it change any ACE on the target object if the ACE holds the protected attribute. To apply new elements to all versions of the file, specify ;* in the object name. Refer to the OpenVMS Guide to System Security for more information on propagation rules.
/EDIT
Invokes the access control list editor (ACL editor) and allows you to modify an ACL interactively. The ACL editor does not allow the asterisk (*) and the percent sign (%) wildcard characters in an object name. You must specify the object whose ACL you are editing.The /EDIT qualifier must be the first qualifier on the command line; other qualifiers can include /CLASS and, if the class is SECURITY_CLASS, you can include the /PROFILE qualifier. Whenever an object does not belong to the FILE class, you also need to specify /CLASS.
See the ACL editor in the OpenVMS System Management Utilities Reference Manual for more information.
/EXCLUDE=(filespec[,...])
Excludes the specified files from the SET SECURITY operation. You can include a directory, but not a device, in the file specification. You cannot use relative version numbers to exclude a specific version./EXPIRED
Modifies the time specified with the /BEFORE or the /SINCE qualifier. The /EXPIRED qualifier selects files according to their expiration dates rather than by the backup, creation, or modification date. (The expiration date is set with the SET FILE/EXPIRATION_DATE command.) By default, files are selected according to their creation date./LIKE=(NAME=source-object-name
Identifies the object from which SET SECURITY should copy security elements. The /LIKE qualifier replaces an object's existing elements with those of the source object. Nopropagate ACEs are not transferred and protected ACEs on the target object are not deleted. Use the /COPY_ATTRIBUTE qualifier with the /LIKE qualifier to copy an object's elements. Refer to the OpenVMS Guide to System Security for information about the special handling of protected and nopropagate ACEs.
[,CLASS=source-object-class] [,PROFILE=TEMPLATE=template-name])The object class of the source object defaults to the class of the target object. When the /CLASS qualifier is omitted, the CLASS keyword defaults to FILE.
The PROFILE keyword applies to security class objects. It identifies which template of the security class you want to copy and modify. See /PROFILE for more information.
/LOG
Controls whether the SET SECURITY command displays the name of the object that has been modified by the command. The qualifier is invalid with the /EDIT qualifier./MODIFIED
Modifies the time value specified with the /BEFORE or the /SINCE qualifier. The /MODIFIED qualifier selects files according to the dates on which they were last modified, rather than by the backup, creation, or expiration date. By default, files are selected according to their creation date./OWNER=identifier
Modifies the owner element of an object. Specify the user identification code (UIC) or general identifier in the standard format. Modifying the owner element of a file usually requires privileges. See the discussion in the OpenVMS Guide to System Security./PROFILE=TEMPLATE[=template-name]
Identifies which template profile of a security class object you want to modify. All object classes except FILE have at least one template profile. These template profiles define the basis of the profile of new objects. Use the DCL command SHOW SECURITY/CLASS=SECURITY_CLASS to display template names. When no value is given for template-name, SET SECURITY uses the template named DEFAULT.Include the /CLASS=SECURITY_CLASS qualifier to identify which profile you want to modify.
/PROTECTION=(ownership[:access][,...])
Modifies the protection code of an object. The protection code defines the type of access allowed to users, based on their relationship to the object's owner.Specify the ownership parameter as system (S), owner (O), group (G), or world (W).
Access types are class specific and are shown in the Description section. For access, use the first letter of the access name. The Examples section provides you with models of protection codes.
/REPLACE=(ace[,...])
Eliminates entries listed with the /ACL qualifier and adds entries listed with the /REPLACE qualifier. SET SECURITY inserts the entries listed with /REPLACE in the position of the last deleted ACE./SINCE[=time]
Selects only those files dated after the specified time. You can specify time as absolute time, as a combination of absolute and delta times, or as one of the following keywords: BOOT, LOGIN, TODAY (default), TOMORROW, or YESTERDAY. Specify the /CREATED or the /MODIFIED qualifier to indicate the time attribute to be used as the basis for selection. The /CREATED qualifier is the default.For complete information on specifying time values, see the OpenVMS User's Manual or the topic SPECIFY Date_Time in online help.
#1
$ SHOW SECURITY LNM$GROUP /CLASS=LOGICAL_NAME_TABLE
LNM$GROUP object of class LOGICAL_NAME_TABLE
Owner: [SYSTEM]
Protection: (System: RWCD, Owner: R, Group: R, World: R)
Access Control List:
(IDENTIFIER=[USER,SMITH],ACCESS=CONTROL)
$ SET SECURITY LNM$GROUP /CLASS=LOGICAL_NAME_TABLE -
_$ /ACL=((IDENTIFIER=CHEKOV,ACCESS=CONTROL), -
_$ (IDENTIFIER=WU,ACCESS=READ+WRITE)) -
_$ /DELETE=ALL -
_$ /PROTECTION=(S:RWCD, O:RWCD, G:R, W:R)
$ SHOW SECURITY LNM$GROUP /CLASS=LOGICAL_NAME_TABLE
LNM$GROUP object of class LOGICAL_NAME_TABLE
Owner: [SYSTEM]
Protection: (System: RWCD, Owner: RWCD, Group: R, World: R)
Access Control List:
(IDENTIFIER=[USER,CHEKOV],ACCESS=CONTROL)
(IDENTIFIER=[USER,WU],ACCESS=READ+WRITE)
#2This example shows how to make a straightforward change to the security elements of an object. The first SHOW SECURITY command displays the current settings of the LNM$GROUP logical name table. The SET SECURITY command resets the ACL to allow control access for user Chekov, and to allow read and write access for user Wu. Note that without the /DELETE=ALL qualifier, these ACEs would have been added to the existing ACL rather than superseding it. The protection is also changed to allow read, write, create, and delete access for the owner. The last command displays the results of the changes.
$ SHOW SECURITY LNM$GROUP /CLASS=LOGICAL_NAME_TABLE
LNM$GROUP object of class LOGICAL_NAME_TABLE
Owner: [SYSTEM]
Protection: (System: RWCD, Owner: R, Group: R, World: R)
Access Control List:
(IDENTIFIER=[USER,FERNANDEZ],ACCESS=CONTROL)
$ SHOW SECURITY LNM$JOB /CLASS=LOGICAL_NAME_TABLE
LNM$JOB object of class LOGICAL_NAME_TABLE
Owner: [USER,WEISS]
Protection: (System: RWCD, Owner: RWCD, Group, World)
Access Control List: <empty>
$ SET SECURITY LNM$JOB /CLASS=LOGICAL_NAME_TABLE -
_$ /LIKE=(NAME=LNM$GROUP, CLASS=LOGICAL_NAME_TABLE) -
_$ /COPY_ATTRIBUTES=PROTECTION
$ SET SECURITY LNM$JOB /CLASS=LOGICAL_NAME_TABLE -
_$ /ACL=(IDENTIFIER=FERNANDEZ, ACCESS=READ)
$ SHOW SECURITY LNM$JOB /CLASS=LOGICAL_NAME_TABLE
LNM$JOB object of class LOGICAL_NAME_TABLE
Owner: [USER,WEISS]
Protection: (System: RWCD, Owner: R, Group: R, World: R)
Access Control List:
(IDENTIFIER=[USER,FERNANDEZ],ACCESS=READ)
#3This example shows how to copy security access information from one object to another and, at the same time, set some elements explicitly. The first SHOW SECURITY commands display the current settings for the LNM$GROUP and LNM$JOB logical name tables. The SET SECURITY command copies the protection code from the LNM$GROUP logical name table to the LNM$JOB logical name table and adds an ACE to allow read access to another user. The final SHOW SECURITY command shows the effect of the changes.
$ SHOW SECURITY SECURITY_CLASS /CLASS=SECURITY_CLASS
SECURITY_CLASS object of class SECURITY_CLASS
Owner: [SYSTEM]
Protection: (System: RWED, Owner: RWED, Group: R, World: R)
Access Control List: <empty>
Template: DEFAULT
Owner: [SYSTEM]
Protection: (System: RWED, Owner: RWED, Group, World: RE)
Access Control List: <empty>
$ SET SECURITY SECURITY_CLASS /CLASS=SECURITY_CLASS -
_$ /PROFILE=TEMPLATE=DEFAULT -
_$ /PROTECTION=(S:RWE, O:RWE, G:RE)
$ SHOW SECURITY SECURITY_CLASS /CLASS=SECURITY_CLASS
SECURITY_CLASS object of class SECURITY_CLASS
Owner: [SYSTEM]
Protection: (System: RWED, Owner: RWED, Group: R, World: R)
Access Control List: <empty>
Template: DEFAULT
Owner: [SYSTEM]
Protection: (System: RWE, Owner: RWE, Group: RE, World: RE)
Access Control List: <empty>
This example demonstrates how to change the security elements for the template of a security class object. The first command shows the current settings for the SECURITY_CLASS object. The second command changes the DEFAULT template of the SECURITY_CLASS object such that the protection is (S:RWE, O:RWE, G:RE). The change is shown in the display of the last command. The world protection of RE remains unchanged.
Controls starting, stopping, and restarting of the security server. The security server maintains information stored in the system intrusion and proxy databases.
SET SERVER server-name
server-name
The server-name must be SECURITY_SERVER.
The SET SERVER command provides a system manager with a means to start, stop, and restart the security server. The security server maintains information stored in the system intrusion and proxy databases.The system intrusion database is used by LOGINOUT, DECnet/OSI, DECwindows, SHOW INTRUSION, DELETE INTRUSION, and other applications. For more information about the system intrusion database and $DELETE_INTRUSION, $SCAN_INTRUSION, and $SHOW_INTRUSION system services, see the OpenVMS System Services Reference Manual. For further information, see the OpenVMS Guide to System Security.
The system proxy database is used by AUTHORIZE, DECnet/OSI, DFS, and other applications to access information stored in the nework proxy database. Additional information can be found in the OpenVMS System Management Utilities Reference Manual. See also the $ADD_PROXY, $DELETE_PROXY, $DISPLAY_PROXY, $VERIFY_PROXY system services in the OpenVMS System Services Reference Manual.
/EXIT
Stop the detached security server process./RESTART
Restart the detached security server process./START
Start the detached security server process.
#1
$ SET SERVER SECURITY_SERVER/START
#2This command starts the detached security server process.
$ SET SERVER SECURITY_SERVER/EXIT
#3This command stops the detached security server process.
$ SET SERVER SECURITY_SERVER/RESTART
This command restarts the detached security server process.
Controls access to local and global symbols in command procedures.
SET SYMBOL
The SET SYMBOL command controls access to local and global symbols in command procedures by treating symbols as undefined. Because all global and local symbols defined in an outer procedure level are accessible to inner procedure levels, it is often necessary to mask these symbols without deleting them.The SET SYMBOL command also controls whether DCL will attempt to translate the verb string (the first token on the command line) as a symbol before processing the line. The default behavior is that the translation is attempted. The advantage to changing this behavior is that a command procedure will not be affected by outer procedure level environments when invoking a command.
The symbol scoping context is different for local and global symbols. Local symbols are procedure level dependent. Local symbols defined in an outer subroutine level can be read at any inner subroutine level, but they cannot be written to. If you assign a value to a symbol that is local to an outer subroutine level, a new symbol is created at the current subroutine level. However, the symbol in the outer procedure level is not modified.
This means that the SET SYMBOL/SCOPE=NOLOCAL command causes all local symbols defined at an outer procedure level to be inaccessible to the current procedure level and any inner levels. For example, if SET SYMBOL/SCOPE=NOLOCAL was specified at procedure levels 2 and 4, procedure level 2 can read (but not write to) only level 2 local symbols. Level 3 can read (but not write to) level 2 local symbols and can read and write to level 3 local symbols. Level 4 can read and write to only level 4 local symbols.
Global symbols are procedure-level independent. The current global symbol scoping context is applied subsequently to all procedure levels. Specifying the /SCOPE=NOGLOBAL qualifier causes all global symbols to become inaccessible for all subsequent commands until either the /SCOPE=GLOBAL qualifier is specified or the procedure exits to a previous level at which global symbols were accessible. In addition, specifying the /SCOPE=NOGLOBAL qualifier prevents you from creating any new global symbols until the /SCOPE=GLOBAL qualifier is specified.
When you exit a procedure level to return to a previous procedure, the symbol scoping context from the previous level is restored for both local and global symbols.
To display the current symbol scoping state, use the lexical function F$ENVIRONMENT("SYMBOL_SCOPE").
/ALL (default)
Specifies that the values of the /SCOPE qualifier pertain both to the translation of the first token on a command line and to general symbol substitution.The /ALL qualifier is incompatible with the /GENERAL or the /VERB qualifier.
/GENERAL
Specifies that the values of the /SCOPE qualifier pertain to the translation of all symbols except the first token on a command line.The /GENERAL qualifier is incompatible with the /ALL or the /VERB qualifier.
/SCOPE=(keyword,...)
Controls access to local and global symbols. Lets you treat symbols as being undefined. Possible keywords are as follows:
NOLOCAL Causes all local symbols defined in outer procedure levels to be treated as being undefined by the current procedure and by all inner procedure levels. LOCAL Removes any symbol translation limit set by the current procedure level. NOGLOBAL Causes all global symbols to be inaccessible to the current procedure level and to all inner procedure levels unless otherwise changed. GLOBAL Restores access to all global symbols. /VERB
Specifies that the values of the /SCOPE qualifier pertain to the translation of the first token on a command line as a symbol before processing only. It does not affect general symbol substitution.
Note
Caution must be used if the SET SYMBOL/VERB/SCOPE command is used more than once in a command procedure. Because DCL uses the translation behavior when looking for a label or subroutine, execution may be different running in one mode than in another. Digital recommends that the SET SYMBOL/VERB/SCOPE command be used once as part of the command procedure setup and left in that mode for the duration of the procedure.
The /VERB qualifier is incompatible with the /ALL or the /GENERAL qualifier.
#1
$ SET SYMBOL/SCOPE=NOLOCAL
#2In this example, all local symbols defined in outer procedure levels are now undefined for the current procedure level and all inner procedure levels.
$ SET SYMBOL/SCOPE=NOGLOBAL
#3In this example, all global symbols are now inaccessible to the current procedure level and all inner procedure levels unless otherwise changed.
$ NOW :== SHOW TIME $ ! $ NOW 7-APR-1994 11:48:58 $ ! $ SET SYMBOL /VERB /SCOPE=NOGLOBAL $ NOW %DCL-W-IVVERB, unrecognized command verb-check validity and spelling \NOW\ $ ! $ SHOW SYMBOL NOW NOW == "SHOW TIME"
This example demonstrates the use of the /VERB qualifier.
The symbol NOW is assigned to the SHOW TIME command. The next line shows the default behavior, where DCL attempts to translate the first string on the command line (NOW). Since NOW translates to the SHOW TIME command, this is used instead of NOW.
The SET SYMBOL command on the next line changes the behavior so that DCL does not attempt a translation. When NOW is subsequently entered, DCL uses the string NOW as the command verb and cannot find it in the command table. This results in the error message.
Notice that the scoping of the verb translation has no effect on general symbol translations, as demonstrated by the SHOW SYMBOL command in the example.
Sets the characteristics of a terminal. Entering a qualifier changes a characteristic; omitting a qualifier leaves the characteristic unchanged.
SET TERMINAL [device-name[:]]
device-name[:]
Specifies the device name of the terminal. The default is SYS$COMMAND if that device is a terminal. If the device is not a terminal, an error message is displayed.
The SET TERMINAL command modifies specific terminal characteristics for a particular application or overrides system default characteristics. (These defaults are defined at each installation, based on the most common type of terminal in use.) The default characteristics for terminals are listed in Figure DCLII-2.The terminal characteristics, local or remote, are determined automatically by the terminal driver for terminals that have the modem characteristic enabled. These characteristics are not affected by the SET TERMINAL command. For example, when you successfully dial in to an OpenVMS system processor, you establish your terminal as remote. When you hang up, the terminal characteristic is set back to local.
The set of terminals supported by the OpenVMS system includes a set of VT100 family terminals that support special Digital ANSI characteristics and escape sequences. For a description of these special characteristics and escape sequences, see the OpenVMS Wide Area Network I/O User's Reference Manual.
Figure DCLII-2 Default Characteristics for Terminals
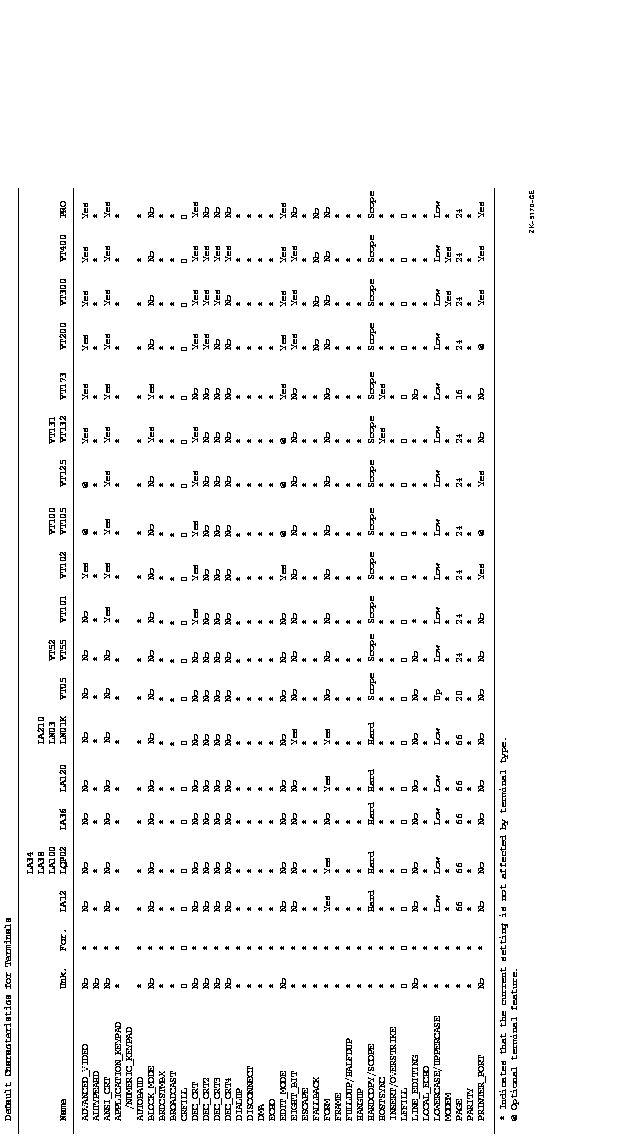

/ADVANCED_VIDEO
/NOADVANCED_VIDEO
Controls whether the terminal has advanced video attributes and is capable of 132-column video. If the terminal width is set to 132 columns and you specify the /ADVANCED_VIDEO qualifier, the terminal page limit is set to 24 lines. If you specify the /NOADVANCED_VIDEO qualifier, the terminal page limit is set to 14 lines./ALTYPEAHD
Causes the terminal driver to create a permanent, alternate type-ahead buffer. The system parameter TTY_ALTYPAHD determines the size of the type-ahead buffer. This specification is effective at your next login and stays in effect until you reboot your VAX computer.To enable /ALTYPEAHD, you must also set the qualifier /TYPE_AHEAD.
You should specify SETTERMINAL/PERMANENT/ALTYPEAHD in SYS$STARTUP:SYSTARTUP_VMS.COM for those communication lines that require this capability.
To use this feature interactively, specify SET TERMINAL/PERMANENT/ALTYPEAHD. This specification is effective at your next login.
/ANSI_CRT (default)
/NOANSI_CRT
Controls whether the terminal conforms to ANSI CRT programming standards. Since ANSI standards are a proper subset of the DEC_CRT characteristics, the default for all VT100 family terminals is /ANSI_CRT./APPLICATION_KEYPAD
Specifies that the keypad is to be set to application keypad mode, which allows you to enter DCL commands defined with the DEFINE/KEY command. By default, the terminal is set to numeric keypad mode./AUTOBAUD
/NOAUTOBAUD
Controls whether the terminal baud rate is set when you log in and sets the default terminal speed to 9600. You must press the Return key two or more times at intervals of at least 1 second for the baud rate to be determined correctly. If you press a key other than the Return key, the /AUTOBAUD qualifier may detect the wrong baud rate. If this happens, wait for the login procedure to time out before continuing. The /AUTOBAUD qualifier must be used with the /PERMANENT qualifier.The valid baud rates are as follows:
50 150 1800 4800 38400 75 300 2000 7200 57600 110 600 2400 9600 76800 134 1200 3600 19200 115200/BLOCK_MODE
/NOBLOCK_MODE
Controls whether block mode transmission, local editing, and field protection are performed./BRDCSTMBX
/NOBRDCSTMBX
Controls whether broadcast messages are sent to an associated mailbox if one exists./BROADCAST (default)
/NOBROADCAST
Controls whether reception of broadcast messages (such as those issued by MAIL and REPLY) is enabled. Specify the /NOBROADCAST qualifier when you are using a terminal as a noninteractive device or when you do not want special output to be interrupted by messages. Use the SET BROADCAST command to exclude certain types of messages from being broadcast, rather than eliminating all messages./COLOR
Sets the ANSI_COLOR terminal characteristic and identifies the terminal as capable of supporting the ANSI color escape sequences./COMMSYNC
/NOCOMMSYNC (default)
Allows connection of asynchronous printers and other devices to terminal ports, using standard modem control signals as flow control. Transmission to the device stops if either data set ready (DSR) or clear to send (CTS) EIA modem control signals are dropped. Transmission resumes when both signals are present.
Previous | Next | Contents | [Home] | [Comments] | [Ordering info] | [Help]
![[HR]](../../IMAGES/REDBAR.GIF)
9996P049.HTM OSSG Documentation 26-NOV-1996 11:18:18.08Copyright © Digital Equipment Corporation 1996. All Rights Reserved.