![[Digital logo]](../../IMAGES/DIGITAL-LOGO.GIF)
![[HR]](../../IMAGES/REDBAR.GIF)
![[Digital logo]](../../IMAGES/DIGITAL-LOGO.GIF)
![[HR]](../../IMAGES/REDBAR.GIF)
Revision/Update Information:
This manual supersedes the OpenVMS System Management Utilities Reference Manual,
OpenVMS Alpha Version 6.2 and
OpenVMS VAX Version 6.2.
Software Version:
OpenVMS Alpha Version 7.1
OpenVMS VAX Version 7.1
Digital Equipment Corporation Maynard, Massachusetts
Possession, use, or copying of the software described in this publication is authorized only pursuant to a valid written license from Digital or an authorized sublicensor.
Digital conducts its business in a manner that conserves the environment and protects the safety and health of its employees, customers, and the community.
© Digital Equipment Corporation 1996. All rights reserved.
The following are trademarks of Digital Equipment Corporation: Bookreader, CI, DBMS, DECdtm, DECevent, DEC Fortran, DECnet, DECserver, DECwindows, DEQNA, Digital, HSC, IAS, InfoServer, LAT, MicroVAX, MicroVAX II, MSCP, OpenVMS, OpenVMS Cluster, PATHWORKS, POLYCENTER, PrintServer, Q-bus, Q22-bus, RA, ReGIS, RK, RL, RSX, RX01, RX02, StorageWorks, TE, TMSCP, TS, TU, TURBOchannel, UDA, UNIBUS, VAX, VAXBI, VAXcluster, VAXstation, VMS, VMScluster, VT100, and the DIGITAL logo.
The following are third-party trademarks:
IEEE and POSIX are registered trademarks of the Institute of Electrical and Electronics Engineers, Inc.
Motif, OSF, and Open Software Foundation are registered trademarks of the Open Software Foundation, Inc.
OSI is a registered trademark of CA Management, Inc.
POSTSCRIPT is a registered trademark of Adobe Systems Incorporated.
All other trademarks and registered trademarks are the property of their respective holders.
ZK6048
The OpenVMS documentation set is available on CD-ROM.
The OpenVMS System Management Utilities Reference Manual contains reference information about the utilities that are used to manage both the OpenVMS VAX and OpenVMS AXP operating systems. This manual describes each system management utility and provides examples for frequently used commands and qualifiers. In addition to system management utilities, a description and usage summary of the AUTOGEN command procedure is presented in this reference manual.
All commands follow the standard rules of grammar as specified in the OpenVMS DCL Dictionary.
For information on how to use these system management utilities and AUTOGEN, please refer to the OpenVMS System Manager's Manual.
This manual is intended for system managers and users of the system management utilities for the OpenVMS VAX and OpenVMS Alpha operating systems.
Each part of this manual, with the exception of the section on the AUTOGEN command procedure, provides reference information for a system management utility.
For additional information on the Open Systems Software Group (OSSG) products and services, access the Digital OpenVMS World Wide Web site. Use the following URL:
http://www.openvms.digital.com
For more information on the system management utilities, refer to the following documents:
Digital welcomes your comments on this manual.
Print or edit the online form SYS$HELP:OPENVMSDOC_COMMENTS.TXT and send us your comments by:
| Internet | openvmsdoc@zko.mts.dec.com |
| Fax | 603 881-0120, Attention: OSSG Documentation, ZKO3-4/U08 |
|
OSSG Documentation Group, ZKO3-4/U08
110 Spit Brook Rd. Nashua, NH 03062-2698 |
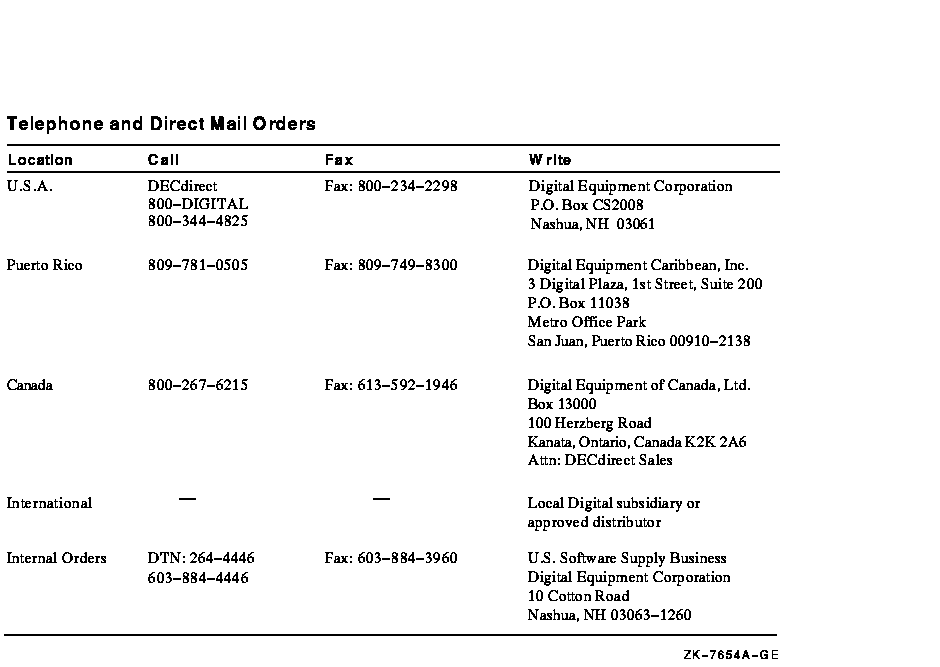
Use the following table to order additional documentation or information. If you need help deciding which documentation best meets your needs, call 800-DIGITAL (800-344-4825).
The name of the OpenVMS AXP operating system has been changed to OpenVMS Alpha. Any references to OpenVMS AXP or AXP are synonymous with OpenVMS Alpha or Alpha.
VMScluster systems are now referred to as OpenVMS Cluster systems. Unless otherwise specified, references to OpenVMS Clusters or clusters in this document are synonymous with VMSclusters.
The contents of the display examples for some utility commands described in this manual may differ slightly from the actual output provided by these commands on your system. However, when the behavior of a command differs significantly between OpenVMS VAX and OpenVMS Alpha, that behavior is described in text and rendered, as appropriate, in separate examples.
In this manual, every use of DECwindows and DECwindows Motif refers to DECwindows Motif for OpenVMS software.
The following conventions are also used in this manual:
| Ctrl/ x | A sequence such as Ctrl/ x indicates that you must hold down the key labeled Ctrl while you press another key or a pointing device button. |
|
PF1
x or
GOLD |
A sequence such as PF1
x or GOLD
x indicates that you must first press and release the key
labeled PF1 or GOLD and then press and release another key or a
pointing device button.
GOLD key sequences can also have a slash (/), dash (--), or underscore (_) as a delimiter in EVE commands. |
| [Return] | In examples, a key name enclosed in brackets indicates that you press a key on the keyboard. (In text, a key name is not enclosed in brackets.) |
| ... |
Horizontal ellipsis points in examples indicate one of the following
possibilities:
|
|
.
. . |
Vertical ellipsis points indicate the omission of items from a code example or command format; the items are omitted because they are not important to the topic being discussed. |
| ( ) | In command format descriptions, parentheses indicate that, if you choose more than one option, you must enclose the choices in parentheses. |
| [ ] | In command format descriptions, brackets indicate optional elem You can choose one, none, or all of the options. (Brackets are not optional, however, in the syntax of a directory name in an OpenVMS file specification or in the syntax of a substring specification in an assignment statement.) |
| [|] | In command format descriptions, brackets indicate optional elements. You can choose one, none, or more than one of the options. (Brackets are not optional, however, in the syntax of a directory name in an OpenVMS file specification.) |
| { } | In command format descriptions, braces indicate a required choice of options; you must choose one of the options listed. |
| text style |
This text style represents the introduction of a new term or the name
of an argument, an attribute, or a reason (user action that triggers a
callback).
This style is also used to show user input in Bookreader versions of the manual. |
| italic text | Italic text indicates important information, complete titles of manuals, or variables. Variables include information that varies in system messages (Internal error number), in command lines (/PRODUCER= name), and in command parameters in text (where device-name contains up to five alphanumeric characters). |
| UPPERCASE TEXT | Uppercase text indicates a command, the name of a routine, the name of a file, or the abbreviation for a system privilege. |
Monospace type
|
Monospace type indicates code examples and interactive screen displays.
In the C programming language, monospace type identifies the following elements: keywords, the names of independently compiled external functions and files, syntax summaries, and references to variables or identifiers introduced in an example. |
| - | A hyphen in code examples indicates that additional arguments to the request are provided on the line that follows. |
| numbers | All numbers in text are assumed to be decimal unless otherwise noted. Nondecimal radixes---binary, octal, or hexadecimal---are explicitly indicated. |
1.1 ACL Editor Description
The access control list editor (ACL editor) is a screen-oriented editor
used to create and maintain access control lists (ACLs). An ACL is a
collection of access control entries
(ACEs) that grant or deny access for specific users or groups of users
of an object. (For a description of the entry and display format for
ACEs, see Section 1.3.) ACLs enable you to control access more closely
than you can by using the default user identification code (UIC) based
protection.
The system does not limit the number of ACEs that an ACL can contain or the number of characters in an ACE. However, long ACLs increase the amount of time necessary to gain access to an object. In practice, memory constraints can limit the size of an ACL.
The order of ACEs in an ACL is important. ACEs granting or denying access to an object for specific users must appear before ACEs identifying broader classes of users. For example, to grant user SMITH read access to a system object and to deny all other interactive users all types of access to the object, place the ACE for user SMITH before the ACE identifying all interactive users on the system.
You can place ACLs on the following object classes:
The access control list editor (ACL editor) creates or modifies an access control list (ACL) for a specified object.
EDIT/ACL object-spec
object-spec
Specifies the object whose access control list is to be created or edited. If an access control list does not exist, it is created.You can specify an object from any of the following object classes:
- Capability
- Common event flag cluster
- Device
- File
- Group global section
- Logical name table
- Queue
- Resource domain
- Security class
- System global section
- Volume
The default object class is a file. A file must be a disk file on a Files-11 On-Disk Structure Level 2 formatted volume. For any object other than a file, you must specify the object class with the /CLASS qualifier.
Note that the ACL editor does not provide a default file type for files. To prevent the ACL editor from using a null file type, specify the file type on the command line. If the object is a directory, specify the .DIR file type.
Do not include wildcard characters in the object specification.
You can invoke the ACL editor to create or modify an ACL for an object that you own, have control access to, or can gain access to by a privilege such as BYPASS, GRPPRV, or SYSPRV. To invoke the ACL editor, enter the DCL command EDIT/ACL. In the command line, specify the name of the object whose ACL you want to edit. For example, to create an ACL for the file INVENTORY.DAT, enter the following command:$ EDIT/ACL INVENTORY.DATYou can use either the EDIT/ACL command or the SET SECURITY/EDIT command to invoke the ACL editor. For more information on the SET SECURITY command, see the OpenVMS DCL Dictionary and the OpenVMS Guide to System Security.
By default, the ACL editor creates and modifies ACLs for files. To create an ACL for an object other than a file (for example, to create an ACL for a queue), you must specify the object class when you invoke the ACL editor. For example, the following command invokes the ACL editor to create an ACL for the disk DAPR:
$ EDIT/ACL/CLASS=DEVICE DAPRIf an ACL for the object you specify already exists, the ACL editor displays the ACL. You can then use keypad editing commands to add, replace, or delete one or more ACEs in the ACL (see Section A.1). To exit from a completed editing session, press Ctrl/Z. To end an editing session without incorporating any of your edits, press the GOLD key (PF1) and then press Ctrl/Z.
For a description of keypad editing commands supplied by the ACL editor, see Appendix A. For information on how to modify the ACL editor by modifying ACL section files, see Appendix B.
Note
In addition to invoking the ACL editor directly or by entering commands at the DCL prompt ($), you can modify an ACL by using the callable interface to the ACL editor (the ACLEDIT$EDIT routine). For information about how to use the ACLEDIT$EDIT routine, see the OpenVMS Utility Routines Manual.
1.3 ACE Formats
This section describes the entry and display format for the following
access control entries (ACEs):
The OpenVMS Guide to System Security describes how to use each of these ACEs. You can also use other types of ACEs. For example, applications can use an Application ACE to store application-specific information associated with a file. For a description of the internal format used to store an ACE, see the OpenVMS Programming Concepts Manual.
Specifies the access criteria that cause an alarm message to be sent to all security operator terminals.ACL alarms are enabled by default; however, alarms are not written to the system security audit log file. If you have existing files or resources protected by Alarm ACEs and you want messages to be recorded in the log file, replace the Alarm ACEs with Audit ACEs.
(ALARM=SECURITY [,OPTIONS=attributes], ACCESS=access-type[+access-type...])
options
Specify any of the following attributes:
Default Indicates that an ACE is to be included in the ACL of any files created within a directory. When the entry is propagated, the Default attribute is removed from the ACE of the created file. This attribute is valid for directory files only. Hidden Indicates that this ACE should be changed only by the application that adds it. Although the Hidden attribute is valid for any ACE type, its intended use is to hide Application ACEs. To delete or modify a hidden ACE, you must use the SET SECURITY command. Users need the SECURITY privilege to display a hidden ACE with the DCL commands SHOW SECURITY or DIRECTORY/SECURITY. SECURITY privilege is also required to modify or delete a hidden ACE with the DCL command SET SECURITY. The ACL editor displays the ACE only to show its relative position within the ACL, not to facilitate editing of the ACE. To create a hidden ACE, an application can invoke the $SET_SECURITY system service.
Protected Protects the ACE against casual deletion. Protected ACEs can be deleted only in the following ways:
- By using the ACL editor
- By specifying the ACE explicitly when deleting it
Use the command SET SECURITY/ACL=(ace)/DELETE to specify and delete an ACE.
- By deleting all ACEs, both protected and unprotected
Use the command SET SECURITY/ACL/DELETE=ALL to delete all ACEs.
The following commands do not delete protected ACEs:
- SET SECURITY/ACL/DELETE
- SET SECURITY/LIKE
- SET SECURITY/DEFAULT
Nopropagate Indicates that the ACE cannot be copied by operations that usually propagate ACEs. For example, the ACE cannot be copied by the SET SECURITY/LIKE or SET SECURITY/DEFAULT commands. None Indicates that no attributes apply to an entry. Although you can create an ACL entry with OPTIONS=None, the attribute is not displayed. Whenever you specify additional attributes with the None attribute, the other attributes take precedence. The None attribute is equivalent to omitting the field. access
Specify any access that is valid for the object class. See the OpenVMS Guide to System Security for a listing of valid access types. For an Alarm ACE to have any effect, you must include the keywords SUCCESS, FAILURE, or both with the access types. For example, if the auditing criterion is a failure to obtain write access to an object, specify the following Alarm ACE:(ALARM=SECURITY, ACCESS=WRITE+FAILURE)
Specifies the access criteria that cause an audit message to be written to the system security audit log file. A message is recorded by default. A message is recorded only if ACL audits are enabled with the DCL command SET AUDIT/AUDIT/ENABLE=ACL.
(AUDIT=SECURITY [,OPTIONS=attributes], ACCESS=access-type[+access-type...])
options
Specify one of the following attributes:
Default Indicates that an ACE is to be included in the ACL of any files created within a directory. When the entry is propagated, the Default attribute is removed from the ACE of the created file. This attribute is valid for directory files only. Hidden Indicates that this ACE should be changed only by the application that adds it. Although the Hidden attribute is valid for any ACE type, its intended use is to hide Application ACEs. To delete or modify a hidden ACE, you must use the SET SECURITY command. Users need the SECURITY privilege to display a hidden ACE with the DCL commands SHOW SECURITY or DIRECTORY/SECURITY. SECURITY privilege is also required to modify or delete a hidden ACE with the DCL command SET SECURITY. The ACL editor displays the ACE only to show its relative position within the ACL, not to facilitate editing of the ACE. To create a hidden ACE, an application can invoke the $SET_SECURITY system service.
Protected Protects the ACE against casual deletion. Protected ACEs can be deleted only in the following ways:
- By using the ACL editor
- By specifying the ACE explicitly when deleting it
Use the command SET SECURITY/ACL=(ace)/DELETE to specify and delete an ACE.
- By deleting all ACEs, both protected and unprotected
Use the command SET SECURITY/ACL/DELETE=ALL to delete all ACEs.
The following commands do not delete protected ACEs:
- SET SECURITY/ACL/DELETE
- SET SECURITY/LIKE
- SET SECURITY/DEFAULT
Nopropagate Indicates that the ACE cannot be copied by operations that usually propagate ACEs. For example, the ACE cannot be copied by the SET SECURITY/LIKE or SET SECURITY/DEFAULT commands. None Indicates that no attributes apply to an entry. Although you can create an ACL entry with OPTIONS=None, the attribute is not displayed. Whenever you specify additional attributes with the None attribute, the other attributes take precedence. The None attribute is equivalent to omitting the field. access
Specify any access that is valid for the object class. See the OpenVMS Guide to System Security for a listing of valid access types. For an Audit ACE to have any effect, you must include the keywords SUCCESS, FAILURE, or both with the access types. For example, if the auditing criterion is a failure to obtain write access to an object, specify the following Audit ACE:(AUDIT=SECURITY,ACCESS=WRITE+FAILURE)
Adds an extra ACE to the ACL for a file created within the directory to which you assign the Creator ACE. The Creator ACE applies only when the following conditions exist:
- The file being created is not owned by the user identification code (UIC) of the process creating the file.
- The process creating the file does not have system privileges.
For example, both of these conditions exist when a process holding a general identifier with the Resource attribute creates a file in a directory owned by that identifier. In this situation, the system adds an extra ACE at the top of the new file's ACL. If a Creator ACE exists in the ACL for the parent directory, the system propagates the access specified in the Creator ACE to the new ACE. If a directory lacks a Creator ACE, the system assigns an extra ACE with a combination of control access and ownership access. A Creator ACE with ACCESS=None suppresses the addition of the extra ACE.
The Creator ACE applies to directory files only.
See the OpenVMS Guide to System Security for more information.
(CREATOR [,OPTIONS=attribute[+attribute...]], ACCESS=access-type[+access-type...])
options
Specify any of the following attributes:
Protected Protects the ACE against casual deletion. Protected ACEs can be deleted only in the following ways:
- By using the ACL editor
- By specifying the ACE explicitly when deleting it
Use the command SET SECURITY/ACL=(ace)/DELETE to specify and delete an ACE.
- By deleting all ACEs, both protected and unprotected
Use the command SET SECURITY/ACL/DELETE=ALL to delete all ACEs.
The following commands do not delete protected ACEs:
- SET SECURITY/ACL/DELETE
- SET SECURITY/LIKE
- SET SECURITY/DEFAULT
Nopropagate Indicates that the ACE cannot be copied by operations that usually propagate ACEs. For example, the ACE cannot be copied by the SET SECURITY/LIKE or SET SECURITY/DEFAULT commands. None Indicates that no attributes apply to an entry. Although you can create an ACL entry with OPTIONS=None, the attribute is not displayed. Whenever you specify additional attributes with the None attribute, the other attributes take precedence. The None attribute is equivalent to omitting the field. access
Specify access types that are valid for files (read, write, execute, delete, and control).
![[HR]](../../IMAGES/REDBAR.GIF)
6048P.HTM OSSG Documentation 26-NOV-1996 12:42:15.61
Copyright © Digital Equipment Corporation 1996. All Rights Reserved.